The use of technology in various aspects of life has increased dramatically in recent years. With the rise of the internet, the amount of data being transmitted and received has increased significantly. As a result, monitoring data usage has become a critical aspect of cybersecurity. In this article, we will discuss the importance of monitoring data usage in Windows and the potential risks associated with not doing so.
Why monitor data usage in Windows?
Windows is a widely used operating system and is present in many devices such as computers, laptops, and mobile phones. The amount of data that is transmitted and received through these devices is substantial, and it is crucial to monitor it to prevent potential security risks.
One of the primary reasons for monitoring data usage is to protect sensitive information. Sensitive information could include personal information such as credit card numbers, bank account details, and social security numbers. If this information is transmitted or received without proper encryption, it could be intercepted by unauthorized individuals and used for malicious purposes.
Another reason to monitor data usage is to detect malware. Malware is malicious software that is designed to cause harm to a device or network. It can be transmitted through infected email attachments, websites, or even advertisements. If malware is present on a device, it can cause a wide range of problems, including data theft, data corruption, and unauthorized access to the device or network.
The importance of monitoring data usage also lies in identifying network anomalies. Network anomalies refer to unexpected changes in the network traffic patterns. These changes can indicate the presence of malware or other malicious activities. For example, if there is a sudden increase in the amount of data being transmitted, it could indicate the presence of malware that is exfiltrating data from the device or network.
How to monitor data in Windows?
There are several ways to monitor data usage in Windows. One of the easiest ways is to use the built-in Task Manager. The Task Manager provides information on the amount of network data that is being transmitted and received. It also provides information on the process that is using the network, which can help in identifying potential security risks.
Another way to monitor data usage in Windows is to use third-party software. There are many software solutions available that can help in monitoring data usage. These solutions provide more detailed information on the amount of data being transmitted and received and can also provide alerts if there are any unusual changes in the network traffic patterns.
Another tool that can be used to monitor data usage in Windows is the Windows Resource Monitor. The Resource Monitor provides information on the amount of network data that is being transmitted and received and also provides information on the process that is using the network. It can also be used to identify potential security risks by displaying any processes that are using a large amount of network resources.
Possible scenarios in which monitoring data usage is important
There are several possible scenarios in which monitoring data usage is important. One scenario is when an employee is using a company device to access sensitive information. In this case, it is important to monitor the data usage to ensure that the sensitive information is being transmitted and received securely and to detect any potential security risks.
Another scenario is when a user is accessing a public Wi-Fi network. Public Wi-Fi networks are often unsecured, which makes them a prime target for hackers. Monitoring data usage in this scenario is important to prevent potential security risks, such as the interception of sensitive information or the transmission of malware.
A third scenario is when a device is infected with malware. In this case, monitoring data usage is important to detect any unusual changes in the network traffic patterns, which could indicate the presence of malware.
GlassWire to monitor your data
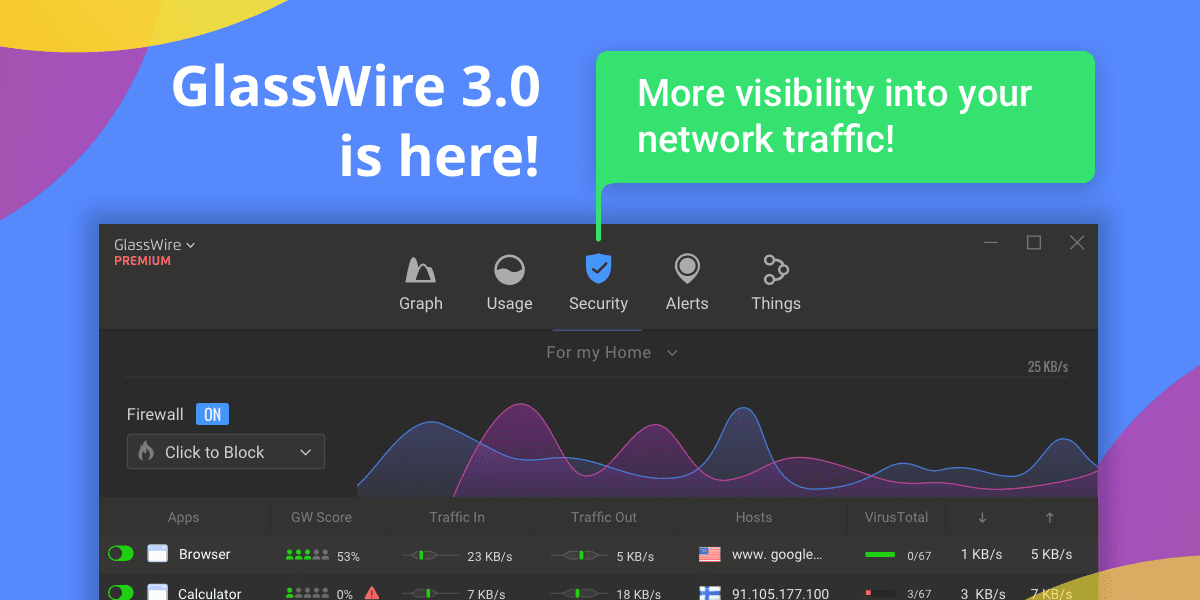
GlassWire is a powerful and user-friendly tool that makes it easier to monitor data usage in Windows. With GlassWire, users can easily view the amount of data that is being transmitted and received, and can also monitor the processes that are using the network. The software provides detailed visualizations of network activity, including graphs and charts that show the amount of data being transmitted and received over time.
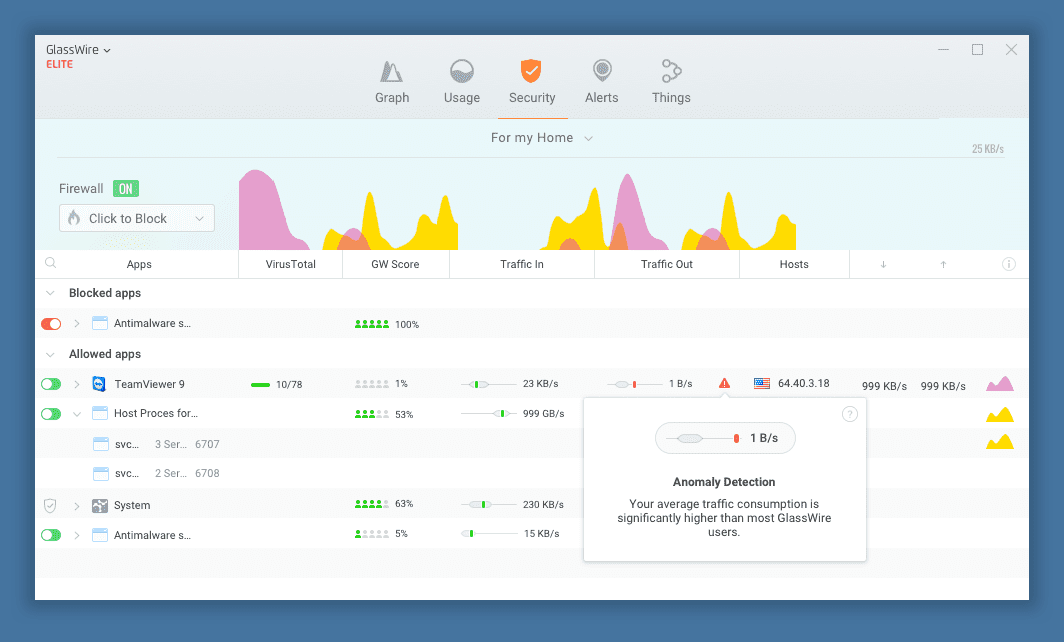
GlassWire also provides alerts for potential security risks. If there is an unexpected change in the network traffic patterns, such as a sudden increase in data usage, GlassWire will alert the user and provide information on the process that is using the network. This allows users to quickly identify and address potential security threats.
Another feature of GlassWire is its firewall. The firewall provides an additional layer of security by controlling which processes can access the network. This helps to prevent unauthorized access to sensitive information and protects against the transmission of malware.
The software also has a privacy mode that allows users to hide their network activity from others. This is useful for those who are using public Wi-Fi networks and want to ensure that their sensitive information is not being intercepted.
GlassWire also has a feature that allows users to monitor data usage on mobile devices. This is useful for those who are using both a Windows device and a mobile device and want to monitor the data usage on both devices from one central location.
In conclusion, GlassWire is an excellent tool for monitoring data usage in Windows. Its user-friendly interface, detailed visualizations, and security features make it easy for users to monitor their network activity and protect against potential security risks. With GlassWire, users can have peace of mind knowing that their sensitive information is secure and that their devices are protected from malware.