People often ask us how we came up with the idea for GlassWire. The answer is, we built GlassWire because it was something we wanted for ourselves for our own PCs. Our team had tested all the different security software out there for our own personal use, but none of it did what we needed.
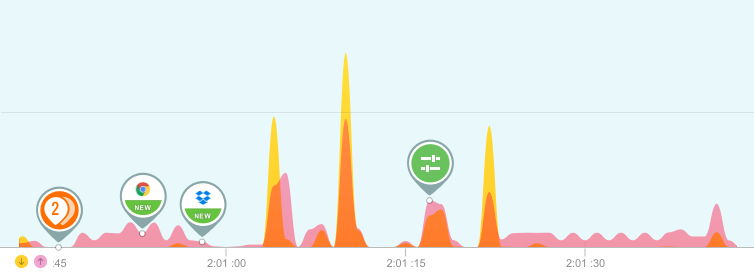
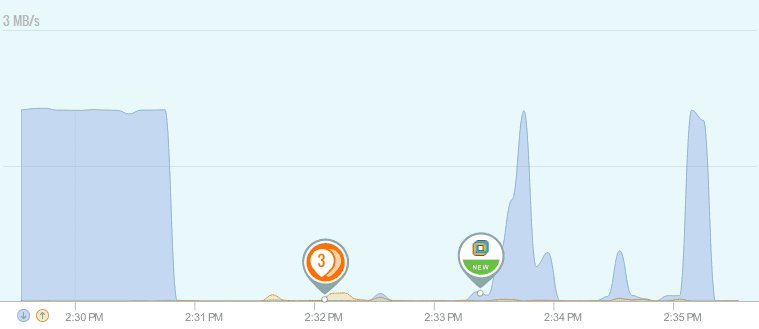
We wanted an application that looked at our PCs and exposed any network related changes that were taking place in real-time. For example, if a network-connected application changes its hash or loses its signed certificate GlassWire tells you. Or any time a new application on your PC accesses the network GlassWire tells you immediately with a “new” alert.
GlassWire also alerts you of software version changes, network related changes to Windows, new proxy connections, DNS server changes, along with letting you know of known suspicious hosts your PC is interacting with.
Our GlassWire theory is that modern malware will almost always make some kind of network related change to your PC. We thought that if we were able to make it easy for normal people to see the network related changes that were happening on their PC then they would be able to catch malware that an antivirus might miss. Also, we wanted to create something that any normal person could use and understand.
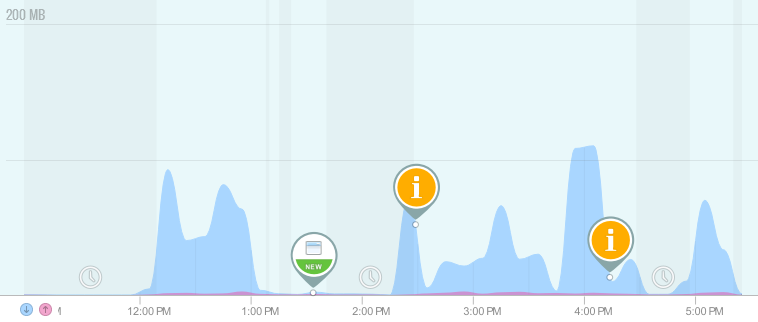
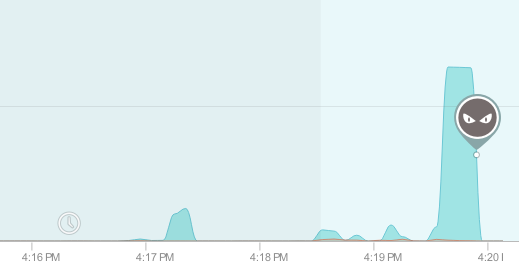
When we launched GlassWire, one of our first users emailed us and let us know he caught malware his antivirus had missed and we blogged about it. The malware was starting new proxy connections from the infected PC and sending out huge amounts of data. These multiple proxy connections and high data usage showed up in the GlassWire graph and warned the user something was wrong (as shown below).
So how can you use GlassWire to look out for possible malware infections? We made a guide in our help area to help people check for malware infections.
First download and install GlassWire, then check the graph and see if you notice anything unusual happening. Are there strange proxy connections when you don’t normally use a proxy? Are there strange applications listed under the GlassWire “firewall” tab? Did your DNS server change after installing that new ‘free’ program? Are you seeing huge amounts of network activity when your PC is idle? These PC behaviors can be a sign something is wrong.
It sounds counter-intuitive if your antivirus is failing you, but we recommend doing an antivirus scan if you’re worried about a problem. Before doing the scan you should make absolutely sure your antivirus is up to date. If your antivirus can’t update because it expired then uninstall it and try another program, or use Windows Defender to scan. Windows Defender is free and part of Windows. Using Windows Defender to scan a second time could be a useful double-check even if your main antivirus is working OK.
If your antivirus doesn’t see anything but you still feel something is wrong you can try using VirusTotal.com to look for malware. VirusTotal checks files against all popular antivirus engines and shows you if any antivirus programs mark your file as suspicious. Look at your GlassWire Firewall tab and find the locations (on your PC hard drive) of any network-related applications that seem suspicious. Click on the icon of the suspicious application and see if it’s signed at all, or signed by someone you recognize.
If the application seems suspicious find its location that GlassWire lists on your PC, then copy the file to your desktop (preferably without moving it) and upload it to VirusTotal.com and see its rating. If VirusTotal shows that several antivirus applications have detected the application as malware, then you might be infected.
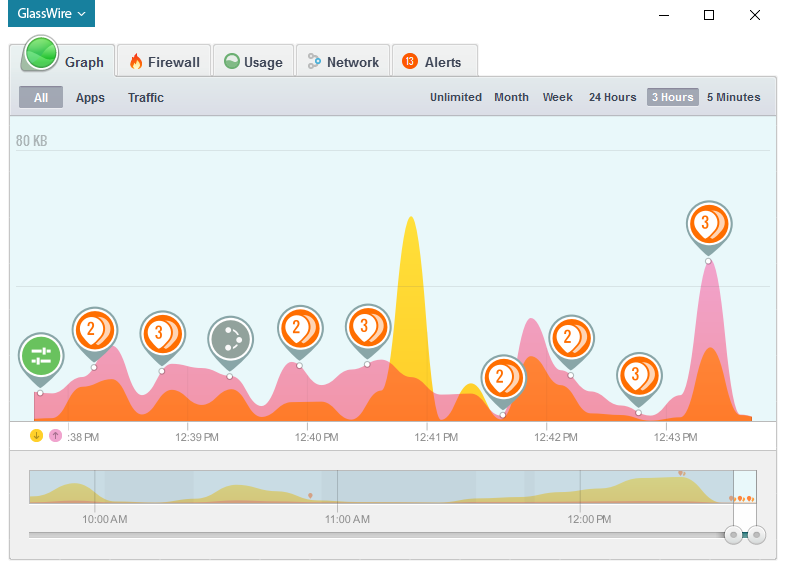
GlassWire also shows the hosts your PC is connecting with in real time. If you see a spike in the GlassWire graph, click the graph to see what apps and hosts are responsible for the increase in network activity.
GlassWire automatically resolves the host names your PC is communicating with in real time, plus you can also check the flag next to the host name to see what country the server is in. For example if the host name shows an American flag the host is probably located in the USA. If you’re unsure about the host you can also type IP addresses in to VirusTotal to check their safety. If nothing shows up in VirusTotal for the host name you entered you can also consider typing the host into Google to see if anything unusual comes up.
Still feeling paranoid? Try Microsoft’s Malicious Software Removal Tool and see if it comes up with anything. And as always, GlassWire fans are glad to give their feedback in our forum any time you need help.
Also please consider upgrading to GlassWire Basic, Pro, or Elite to block all new connections with our paid Ask to connect mode.
Unfortunately there is no perfect tool for detecting and removing malware, but we hope this guide helps you understand how to use GlassWire to look for suspicious activity.