Every 39 seconds, a cyberattack happens. Now, think about your passwords, bank details, and personal data. How secure do you think they are?
In this post, you will learn about cybersecurity basics and the must-do steps to safeguard your data against cyber threats and keep your privacy in tip-top shape.
Find it hard where to start? Let’s get into it.
What Is Cybersecurity?
Cybersecurity is the practice of protecting computer systems, networks, and data from malicious attacks or unauthorized access. It uses tools like personal firewalls and intrusion detection systems to make sure your information stays secure and isn’t misused.
If something goes wrong, knowing cybersecurity basics helps you act fast. Once a hacker manages to break into your system, cybersecurity measures will help you figure out what happened, fix the issue, and prevent it from happening again.
6 Basic Terminologies of Cybersecurity
To understand this topic more easily, learn these basic terms:
- Firewall: is a security system that monitors incoming and outgoing network traffic to make sure only safe and approved data gets through
- MAC Address: short for Media Access Control, MAC address is a unique identifier to pinpoint devices on a local network and facilitate the correct data routing
- Penetration Testing: is a proactive security practice to assess the network’s endpoint security and identify potential threats before malicious attackers exploit user data
- Domain Name Server (DNS): translates domain names like www.example.com into IP addresses to make it easier for your browser to search for trusted websites
- Virtual Private Network (VPN): a VPN encrypts your internet traffic and hides your IP address to keep your online activities more private
- Internet Protocol (IP) Address: is a unique string of numbers separated by periods or colons (like 192.0.2.1) that identifies the host or network interface and provides the location of the host in the network
5 Types of Cybersecurity Threats
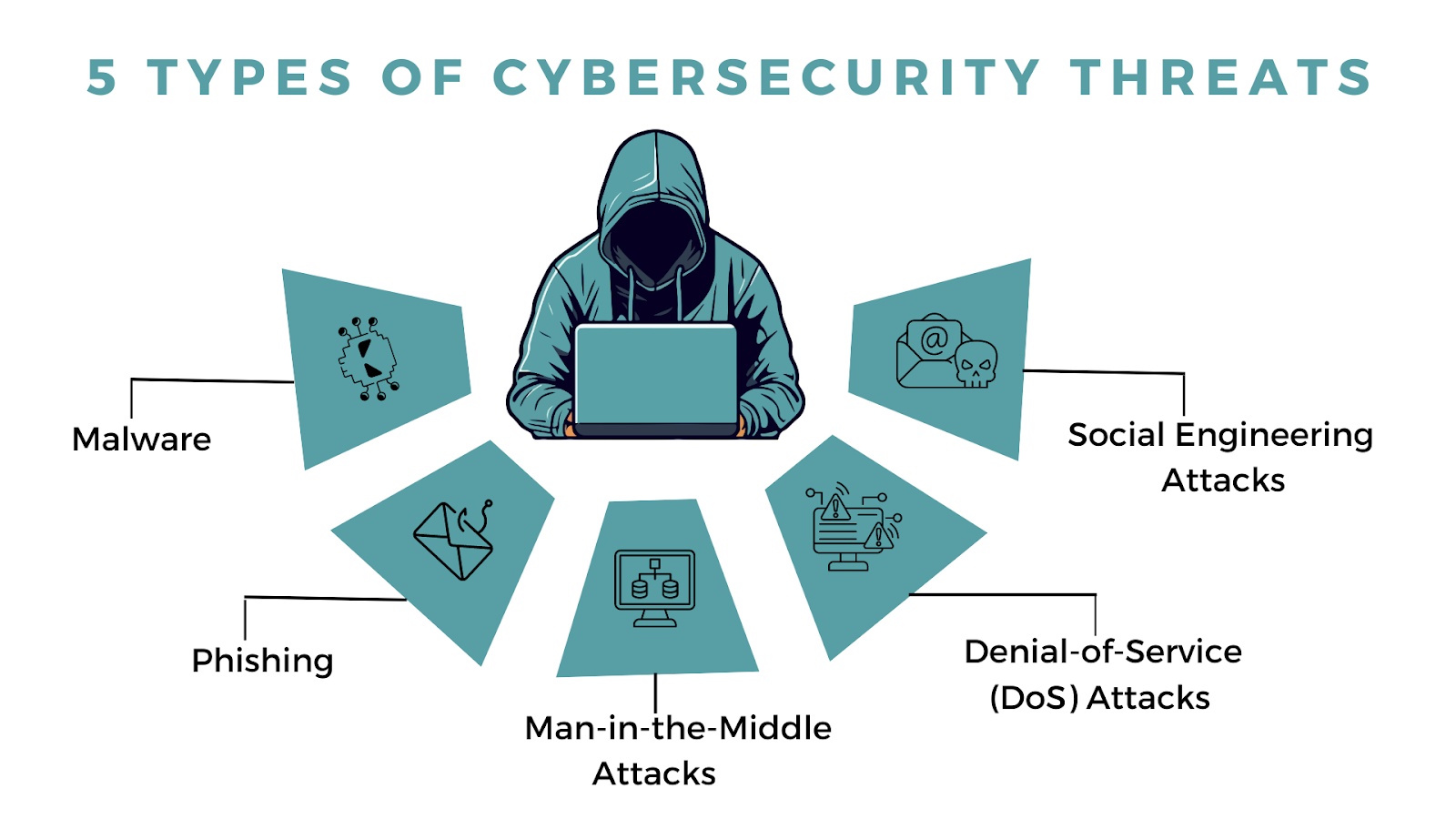
53% of adults do not know how to protect themselves from cybercrime. As you explore these threats, assess what makes your company vulnerable to cyber attacks so you will be ready to take in the best practices needed.
1. Malware
Malware is short for malicious software that often hides in fake emails or shady downloads without you even noticing. Once it gets in, it can steal your data, lock you out of your files, or even hijack your entire system. To keep your business safe and running, update your software as often as needed, use strong antivirus programs, and be wary of suspicious emails.
Here are the types of malware to watch out for:
- Viruses: are malicious code that attaches itself to legitimate programs and spreads when those programs are executed
- Worms: are self-replicating malware that distributes through networks without needing a host file
- Trojans: they disguise themselves as useful software, but once installed, they allow hackers to access your security systems
- Adware: it bombards you with unwanted ads. It can slow down your computer network and track your browsing habits
- Spyware: secretly watches your online activities and collects user information without consent
2. Phishing
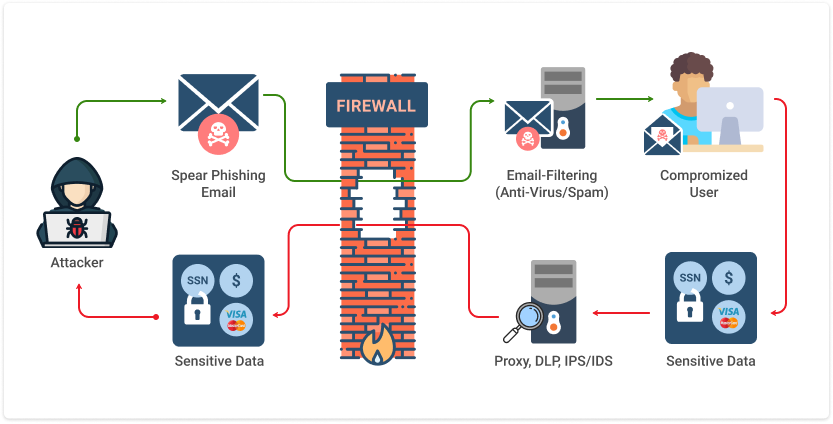
Phishing tricks you into giving away your personal information by pretending to be someone you trust. In 2023, 71% of businesses experienced a phishing attack, and many fell for them because they looked incredibly legitimate. The impact? 1 wrong click triggers an average $4.76 million data breach cost globally, which is higher than $4.45 million in 2023.
3. Man-in-the-Middle (MitM) Attacks
MitM attacks happen when someone secretly intercepts and relays communications between 2 parties who believe they are directly communicating with each other. The attacker eavesdrops, alters, and steals sensitive information like login credentials, financial data, or personal information.
4. Denial-of-Service (DoS) Attacks
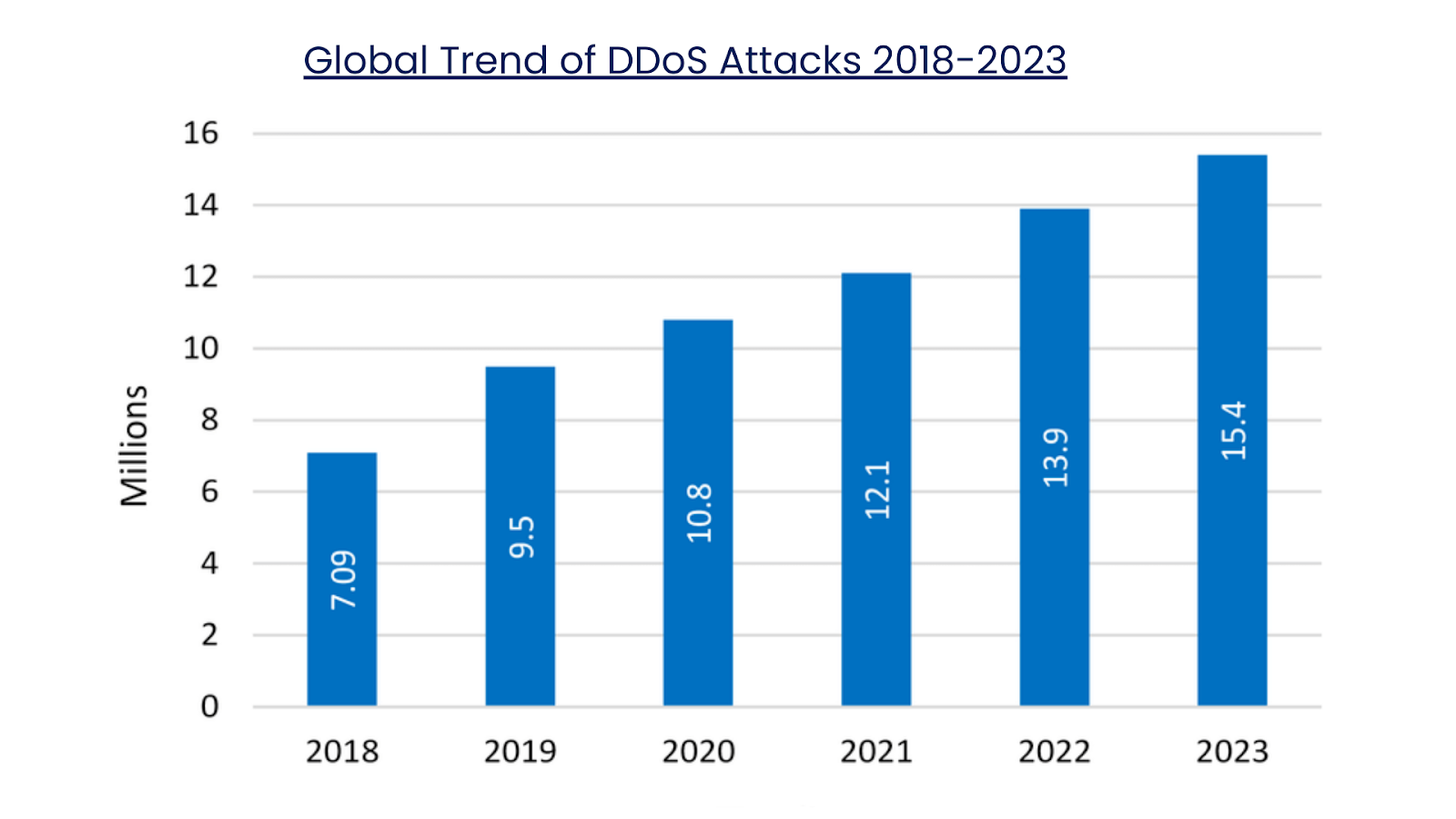
A Denial-of-Service (DoS) attack makes a website or online service stop working. They flood the site with so much traffic or data that it slows down or crashes. In 2023, there were over 15 million DoS attacks worldwide, and a single minute of downtime during a DoS attack can cost businesses around $5,600.
5. Social Engineering Attacks
Instead of breaking into your network systems, social engineering attacks use different schemes to manipulate users. For instance, a scammer might pretend to be a tech support agent to ask for your account details. If you fall for it, they could steal your money or access your accounts.
Here’s a closer look at the different types of social engineering attacks:
- Baiting: offers something enticing that actually contains malware
- Vishing: uses spam phone calls and pretends to be from legitimate organizations
- Smishing: sends fraudulent text messages that look like they’re from trusted sources
Cybersecurity Basics: 12 Best Practices You Need to Know

As you go through each practice, jot down the specific action points you need to learn about cybersecurity basics and see what changes you can make to stay more secure online.
1. Use Strong, Unique Passwords
Let’s admit it. Many of us struggle to remember all our passwords at once. A staggering 81% of data breaches involve weak, reused, or stolen passwords. Since 2022, Norton says hackers have exposed over 24 billion passwords, and password hacking statistics show that 1 million passwords are stolen every week.

Hackers can easily guess or crack weak passwords and put your sensitive information at risk. As you sign up for an account or want to review your existing passwords, here are the key strategies to consider:
- Create a strong password that is at least 8 characters long and uses a mix of letters, numbers, and special characters.
- Avoid using easily guessed passwords like “password123” or the default “admin.”
- Opt for a password manager like NordPass to generate and store complex passwords without needing you to memorize them.
- Use online password checker tools like “Have I Been Pwned?” to find out if your passwords or even email address are compromised for data breaches.
2. Enable Two-Factor Authentication (2FA)
Two-Factor Authentication (2FA) adds an extra layer of network security. That means even if a hacker gets your password, 2FA requires a second authentication, like a code sent to your phone or email address, before they access your account. Microsoft found that implementing 2FA blocks 99.9% of automated attacks.
Here’s how to set up your 2FA:
- Sign in to the account you want to secure (ex., email, social media, banking).
- Open the account settings or network security settings section. Look for options labeled as “Two-Factor Authentication,” “Two-Step Verification,” or “Multi-Factor Authentication.”
- Follow the prompts to enable 2FA. You may need to enter your password again for security purposes.
- Choose your preferred authentication method. Google Authenticator, Microsoft Authenticator, or Authy are common apps that generate a time-sensitive code that you enter when logging in. If available, you can use a physical security key that connects to your device via USB or NFC.
- Use unique passwords for each account and consider using a password manager to keep your passwords in one place and place them instant when logging in.
3. Be Cautious With Free Wi-Fi

Free Wi-Fi is tempting, but it can be risky. Public Wi-Fi networks can be a playground for hackers. Sure, when you connect to an unsecured network, you’re opening the door for cybercriminals to intercept your data.
If you can’t avoid using free Wi-Fi, use a Virtual Private Network (VPN) to secure your internet connection and make it difficult for hackers to intercept your data. Still, avoid accessing sensitive accounts, like banking or email, while connected to public Wi-Fi.
Make sure to “forget” the network on your device after you’re done to prevent your device from automatically reconnecting to it in the future.
4. Keep Software Up-To-Date
Software updates are not just about getting the hype of the latest features. They include data security patches that block the potential threats we mentioned above. When you use outdated software platforms, you risk exposing your devices to cyber attacks because hackers usually exploit weaknesses in older versions.
On top of that, you can experience slower response times, increased crashes, and poor overall user experience. Worse, you may notice that your applications or software become sluggish or unresponsive over time.
5. Avoid Clicking Suspicious Links Or Emails
Phishing spurs around 3.4 billion spam emails sent globally every day. Cybercriminals use phishing scams to trick you into clicking malicious links or attachments with too-good-to-be-true offers until you give up your personally identifiable information (PII).
So, if something looks off, trust your gut and don’t click just yet. Hover over links to check the URL before clicking. Avoid clicking on shortened URLs that hide their real intent. Phishers even use email addresses that look similar to legitimate ones but with slight variations in spelling, numbers, or special characters. Verify the sender’s address to make sure it’s from a trusted source.
6. Back Up Your Data Daily Or 1x a Week

If ransomware or a hardware failure wipes out your data, having a backup means you won’t lose everything. With the growing 48% statistics of small businesses that suffer from a cyber attack, 60% of them go out of business within 6 months because they don’t have a data backup plan. To avoid this, secure a strong backup strategy to save your organization from severe data loss.
Start creating daily backups of your sensitive data, like documents, photos, and financial records. Store them on an external hard drive or in a secure cloud storage service, and test your backups periodically to make sure they are working as expected and that you can restore your data anytime you need.
7. Install & Update Antivirus Software

Your antivirus software is like a security camera for your computer. If it’s outdated, it might miss spotting new types of malware that pop up all the time. Every day, the AV-TEST Institute logs over 450,000 new malicious programs.
With over 4.5 billion internet users worldwide, cybercriminals have a vast pool of targets. To safeguard your system, make sure to do a full scan of your network operating systems to detect and remove any malware infections that might have slipped through.
GlassWire pairs well with any antivirus software. Its built-in firewall monitors and scans your network activity in real-time. With an easy-to-read interface, the platform detects suspicious network activity and alerts you to potential threats before they cause harm.
8. Enable Pop-Up Blockers
Pop-ups can be a gateway to malware or phishing sites. To help prevent these cyber threats, enable pop-up blockers in your web browsers. 83% of websites have security vulnerabilities that could be exploited by pop-up ads.
You can stop those intrusive pop-ups from malicious sites with these steps:
- Go to your web browser’s settings and enable the pop-up blocker feature to prevent unwanted pop-ups from appearing.
- Even if a site seems reliable, pop-ups from these sites can still carry malicious software. Be careful when allowing pop-ups from any site.
- Use an ad-blocking extension or plugin to add an extra layer of protection against unwanted ads and pop-ups.
- Adjust your browser’s privacy settings to limit data sharing with third-party sites, adding another layer of security.
9. Manage Permissions & Access
Be selective about who you share your information with. If something seems off, stay cautious and use strict access controls to limit what others can do. Only give people the access they need to do their job. For example, if someone’s role changes, update their access accordingly.
Research shows that businesses that implement strict access controls can reduce the risk of data breaches by up to 70%. Use built-in groups and teams to assign permissions at different levels (ex., owners, members, visitors). Limit external sharing and enable it only when necessary, with appropriate restrictions (ex., guest accounts or expiration dates). Hire a system administrator to handle this for you.
10. Clear Cookies & Cache
Your browser’s cookies and cache are the digital breadcrumbs that websites leave on your computer or mobile device. It stores information about your online activity, including login credentials, browsing history, and personal preferences. Clear them at least once a month or more often as needed to keep your browser running smoothly.
It also improves your device’s performance and speeds up your browsing experience. To avoid storing cookies and cache, use your browser’s incognito or private mode for sensitive activities. Consider using a privacy-focused web browser or a virtual private network (VPN) for an extra layer of protection.
11. Review Privacy Settings
Reviewing and adjusting your privacy settings helps control what information you share online. A Pew Research Center survey found that 74% of people worry about how their data is collected and used.
Your devices and online accounts use privacy settings that determine what information you share and who can see it. Frequently review and adjust these settings to avoid oversharing your sensitive data and reduce the risk of identity theft and other privacy issues.
12. Educate Yourself On Phishing Scams
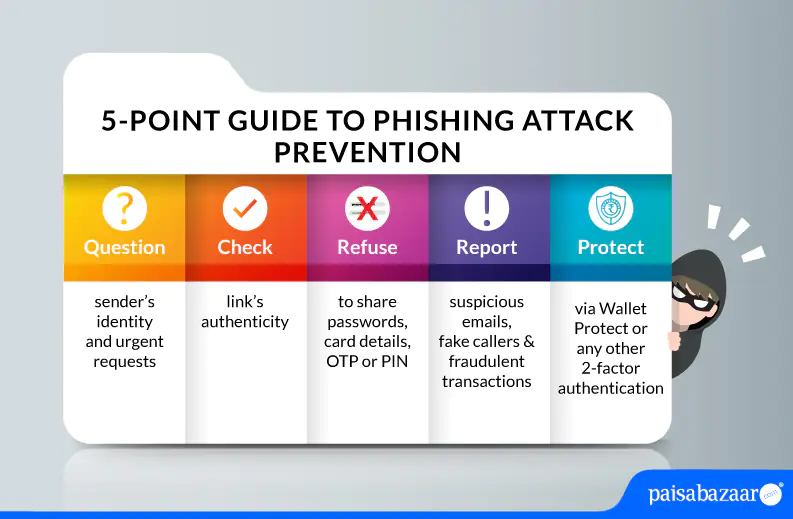
Phishing scams are constantly evolving, so staying informed helps you spot the latest tactics and loopholes. 97% of people can’t identify a sophisticated phishing email, highlighting the need for ongoing learning about cybersecurity basics:
- Take advantage of free resources like online courses and security blogs.
- Learn to recognize the signs of a phishing scam, like urgent requests for information, suspicious links or attachments, and impersonation of trusted organizations.
- Be cautious of unsolicited emails, messages, or phone calls asking for sensitive information.
- Report any suspected phishing attempts to the appropriate authorities like the chief information security officer with cybersecurity certifications.
Recent Trends About Cybersecurity In 2024
Artificial intelligence (AI) continues to make significant strides in cybersecurity. In 2024, online security tools for businesses continue to evolve, with solutions like the Sophos XG Firewall helping to detect and respond to cyber threats up to 60% faster than traditional security solutions.
However, AI’s growing role in cybersecurity is a double-edged sword. Cybercriminals also use AI to create more sophisticated digital attacks. Ransomware incidents, for instance, increased by 35% in the first half of 2024. This surge in cybercrime pushed global ransomware damages to over $42 billion in 2024, up from $20 billion in 2021.
This means you should stay proactive in adopting AI-powered security tools to keep up with evolving threats. At the same time, boost employee awareness and cybersecurity protocols to defend against these advanced attacks.
Conclusion
Now that you have the lowdown on cybersecurity basics, it’s time to take action. Review your current security measures—what’s working well, and where do you need improvement?
Refine your existing cybersecurity strategies and make those small tweaks to make sure you’re always prepared for what’s next. Cybersecurity isn’t a one-time effort, so continuously monitor your network and adjust your strategies as new threats emerge.
Ready to take your cybersecurity to new heights? GlassWire is here to help you visually track your data usage and alert you to any suspicious network activity.
Author Bio:
Sarah Mitchell is a freelance writer dedicated to producing premium blog content for entrepreneurs and SMBs. Her work helps them streamline their content marketing and you may recognize her name from platforms like Hubspot, Outbrain, Flippa, and many more.




